Snort Rules - A more advanced and practical example

So you have written a few basic rules for Snort, but are you looking for something a bit more indepth? Hopefully this quick tutorial will get you on your way.
For example, here is a basic rule:
alert tcp any any -> any 502 (msg:"Modbus traffic!"; sid:1111101;)
Now lets go a bit further, and using an industrial protocol called modbus, I have created this capture to illustrate this example:
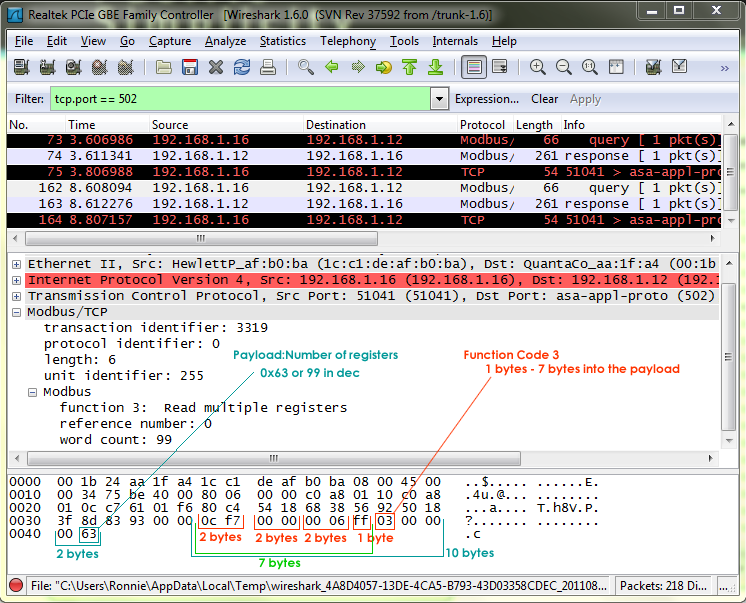
From the image you can see that the Modbus Function Code is 7 bytes in and is 1 byte long - so to create a rule that checks for Function Code 3, you use the following payload checking options:
- content - what you are looking for
- offset - where to start looking
- depth - when to stop looking
Here is the rule that now checks for FC 3:
alert tcp any any -> any 502 (msg:"Modbus FC 3 registers"; content:"|03|";offset:7;depth:1;sid:1111101;)
Continuing on, lets check and the number of registers using the byte_test option. I want to check and see that the number of registers being requested is under 100, note that register 0 counts so we will only be checking to 99 or 0x63 in hex. 100 in decimal will be 0x64!
So we are going to look for 2 bytes that are valued at less than 100 in decimal and are located 10 bytes into the packet payload.
alert tcp any any -> any 502 (msg:"Modbus FC 3 registers"; content:"|03|";offset:7;depth:1;byte_test:2,<,100,10;sid:1111101;)
But wait! We are not done, lets have this rule check only for established sessions from the client!
alert tcp any any -> any 502 (flow:established, from_client; msg:"Modbus FC 3 registers"; content:"|03|";offset:7;depth:1;byte_test:2,<,100,10;sid:1111101;)
From what I can decipher is that the established flag is just checking for an Ack flag, but I might be wrong. However, there is still one problem remaining, we don't want an alert for every single packet that matches.. so lets set a threshold.
alert tcp any any -> any 502 (flow:established, from_client; msg:"Modbus FC 3 registers"; content:"|03|";offset:7;depth:1;byte_test:2,<,100,10;threshold:type threshold,track by_src,count 5,seconds 60;sid:1111101;)
The alert threshold is specified by the threshold option. We want it to track by source IP, but you can use the destination IP or both. Each time the rule is triggered within 60 seconds, a counter will be incremented until it hits the defined value of 5. When 5 is reached, an alert will be generated again. However, the first time the rule is triggered, an alert will be generated regardless.
Hope this helps, happy rule making!
Blog tags:
| Attachment | Size |
|---|---|
| 253.89 KB |
Add new comment